-
MenuBack
-
Products
-
-
-
-
-
-
Municipal services and retail
- All-in-One Touch Computers & Kiosks
- iCity Service & iRetail Solution
- POS & Tablets
- Signage & Edge Computers
-
Connections
-
Cellular Routers and Gateways
- 4G & 5G Entry Level Industrial Routers - ICR-2000
- 4G Powerful Routers - ICR-3200 & SmartFlex
- 5G & 4G Connectivity Gateways - ICR-1000
- 5G & LTE Advanced High Speed Routers - ICR-4000
- Accessories
- Antennas
- Dual Module 4G Routers
- EN 50155 Railway 4G Routers
- Entry Level 4G Routers
- Entry Level 4G Routers & IoT Gateways
- Flexible 4G Routers & IoT Gateways
- High Speed 4G/5G Routers & Edge Computing Gateways
- Industrial LAN Routers (Wi-Fi Optional)
- Modular 3G Routers
- Modular 4G Routers
- Power supplies
- Robust 4G Routers & IoT Gateways
- Software
- Wired LAN Routers
- Ethernet / Serial Device Servers
- Fiber & PoE Converters, Injectors, Extenders
-
Industrial Ethernet Switches
- EN50155 Ethernet Switches
- EN50155 Ethernet Switches: EKI-9500
- IEC61850-3 Ethernet Switches
- Industrial PoE Switches & Solutions
- M12 Ethernet Switches: EKI-9500
- Managed Ethernet Switches
- Managed Ethernet Switches (Entry-level)
- Managed Ethernet Switches (Entry-level): EKI-5000
- Managed Ethernet Switches: EKI-5700/7000/8000/9000
- Managed Ethernet Switches: EKI-7000/8000/9000
- N-Key automatic backup and restore
- Unmanaged Ethernet Switches
- Unmanaged Ethernet Switches: EKI-2000/5000
- Industrial Protocol Gateways
- Industrial Wireless and Gateways
-
Serial Communication
- Serial Communication Cards
-
Serial Converters/Isolators/Repeaters - ULI-200
- Data Tap/Splitter/Port Combiner - ULI-250/260
- RS-232 Isolated Repeater/Isolator - ULI-232 Series
- RS-232 to RS-422 Converters - ULI-223 Series
- RS-232 to RS-422/485 Converters - ULI-224 Series
- RS-232 to RS-485 Converters - ULI-226 Series
- RS-232/422 to TTL/Current Loop Converter - ULI-227
- RS-422/485 Isolated Repeaters - ULI-234 Series
- Serial Surge Suppressors - ULI-240 Series
- Serial to Fiber Converters - ULI-210 Series
- USB Converters/Isolators/Hubs - ULI-300/400
- Telematics Converters and Gateways
-
Cellular Routers and Gateways
-
-
-
Industrial automation
-
Industrial Automation
- Automation Controllers & I/O
- Certified Solutions
- Class I, Division 2 Solution
-
Data Acquisition (DAQ)
- 3U Communication Boards (MIC-3600 Series)
- 3U Data Acquisition and Control Boards (MIC-3700 Series)
- DAQ Cards
- DAQ-embedded Computer/Module
- DAQNavi
- GPIB
- iDoor Module(Mini PCIe)
- ISA DAQ Cards
- Modular DAQ System
- PC-104/PCI-104 DAQ & Communication Cards
- Signal Conditioning Modules and Terminal Boards
- USB Modules
-
Embedded Automation Computers
- Advantech iDoor Module
- Compact Embedded Box IPC
- Compact Embedded Box PC
- Din-Rail Automation Computer, UNO-1 Series
- Din-Rail Control IPC
- Expandable Automation Computer
- Expandable Automation Computer, UNO-3 Series
- Explosion-Proof Computer
- Industrial IoT Edge Gateway
- Rackmountable Automation Computers for Power Substations
- Standmount Embedded Box PC, UNO-2 Series
- UNO Accessories
- Gateways & Remote Terminal Units (RTUs)
- Human Machine Interfaces
- Machine Automation
- Panel PC
- Power & Energy
- Remote I/O
- SoftLogic Software
- Software Development Kits
- WebAccess Software & Edge SRP
- Wireless I/O & Sensors
-
Industrial Automation
-
Certified peripherals
-
Certified Peripherals
- Active CPU Cooler
- CPU
- Display
- DRAM Memory Module
- Expansion Card
- Flash Card
- Graphics Card
- Hard Drive
- Keyboard
- Mobile Rack
- Mouse
- Network Card
- Optical Drive
- Passive CPU Cooler
- Power Supply
- Rackmount Kit
- RAID Controller
- Software
- Solid State Drive
-
Certified Peripherals
-
Embedded computing
-
Embedded Computing
- AIoT Software, Distribution & Services
- Application Focus Embedded Solutions
- Arm-Based Computing Platforms
- Cable Accessories
- Computer On Modules
- Digital Signage Players
- Edge AI & Intelligence Solutions
- Embedded PCs
- Embedded Single Board Computers
- Embedded Software
-
Fanless Embedded Computers
- ARK Ultra Rugged Series
- ARK-1000 Series: Ultra Slim Fanless Embedded Computers
- ARK-2000 series : Easy I/O Flexibility Fanless Embedded Computers
- ARK-3000 Series: High Performance Fanless Embedded Computers
- ARK-6300 Series: Mini-ITX Series Fanless Embedded Computers
- ARK-7000 Series: Extreme Performance Edge Servers
- iDoor Module Mini PCIe Expansion Kit
- Storage Modules
- Gaming Platform Solutions
- Industrial Display Systems
- Industrial Flash & Memory Solutions
- Industrial Motherboards
- Industrial Wireless Solutions
- Wireless ePaper Display Solutions
-
Embedded Computing
-
-
-
-
-
-
-
Ethernet Extenders
-
Industrial routers
-
-
-
Wireless & Cellular
-
Modems
-
Accessories
-
-
-
-
-
-
-
Ethernet switches
-
-
-
Media convertors
-
Industrial connectivity
-
-
-
Wireless data transfer
-
-
-
-
-
-
-
Routers and Gateways
-
-
-
Icom Connectivity Suite
-
-
-
Icom Data Suite
-
-
-
-
-
- About us
- News
- Industrial areas
- Services
- References
- Support
- Contact
Anomaly detection in OT networks: a key defence
Operational Technology (OT) forms the backbone of many industrial operations in today's world. From energy to transportation to manufacturing, OT systems ensure the automated control of critical processes that keep our infrastructure running. However, with the growing integration of digital technologies into OT networks, the vulnerability of these systems to cyber threats is also increasing. Anomaly detection in OT networks is thus becoming a key defense against potential attacks. And this is where the company Westercom s.r.o. enters the scene.
What is anomaly detection?
Anomaly detection is the process of identifying unusual patterns in data that may signal potential threats or errors in the system. In the context of OT networks, anomaly detection can reveal discrepancies indicating that the system has been attacked, misconfigured, or that other issues are occurring that may result in outages or equipment damage.
Why is anomaly detection in OT networks so important?
In the industrial sector, even small errors can cause significant problems. A minor fault in the energy network can lead to extensive power outages, while an issue in a production line can halt manufacturing and cause financial losses, and in passenger transportation, potential tragedies are easily imaginable. Cyberattacks on OT networks can have catastrophic consequences if not detected and addressed in time.
How will we help with anomaly detection?
We provide highly specialized anomaly detection services in OT networks. Thanks to a deep knowledge base in the field of OT and cybersecurity, we can offer our customers the following benefits:
-
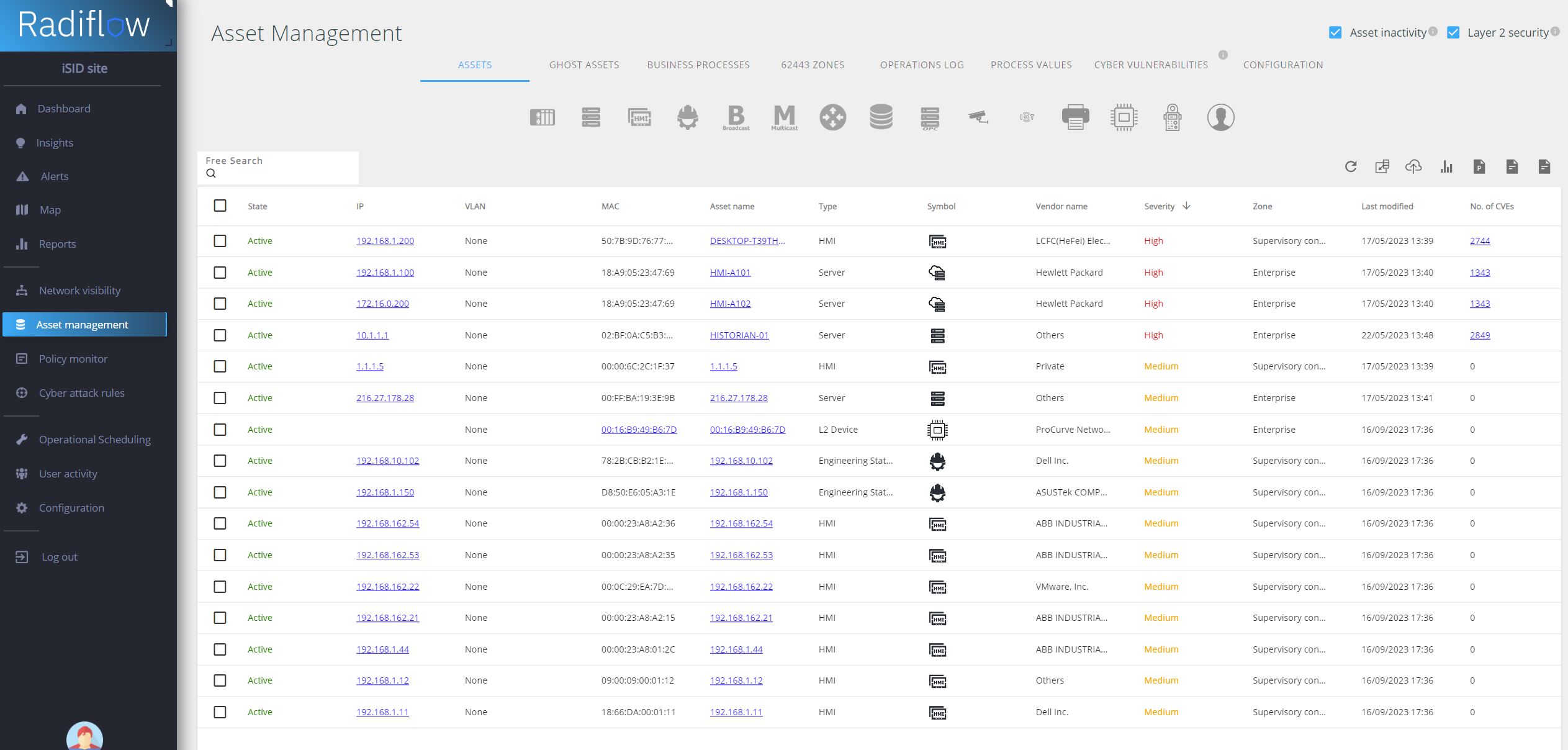
Asset Management: This Asset Management platform represents a revolutionary solution for effective management and monitoring of connected IT resources. You can systematically categorize and filter all system assets, from PLCs to broadcasting stations. With advanced automatic detection technology iSID, we can identify and classify various types of assets (including unwanted or dangerous ones), providing users with the flexibility in customizing labels and adding their own types. Information about potential vulnerabilities is automatically provided for all found connected devices. Our platform is designed to meet the needs of IT professionals, ensuring optimal management and security of your resources, while being simple and clear.
-
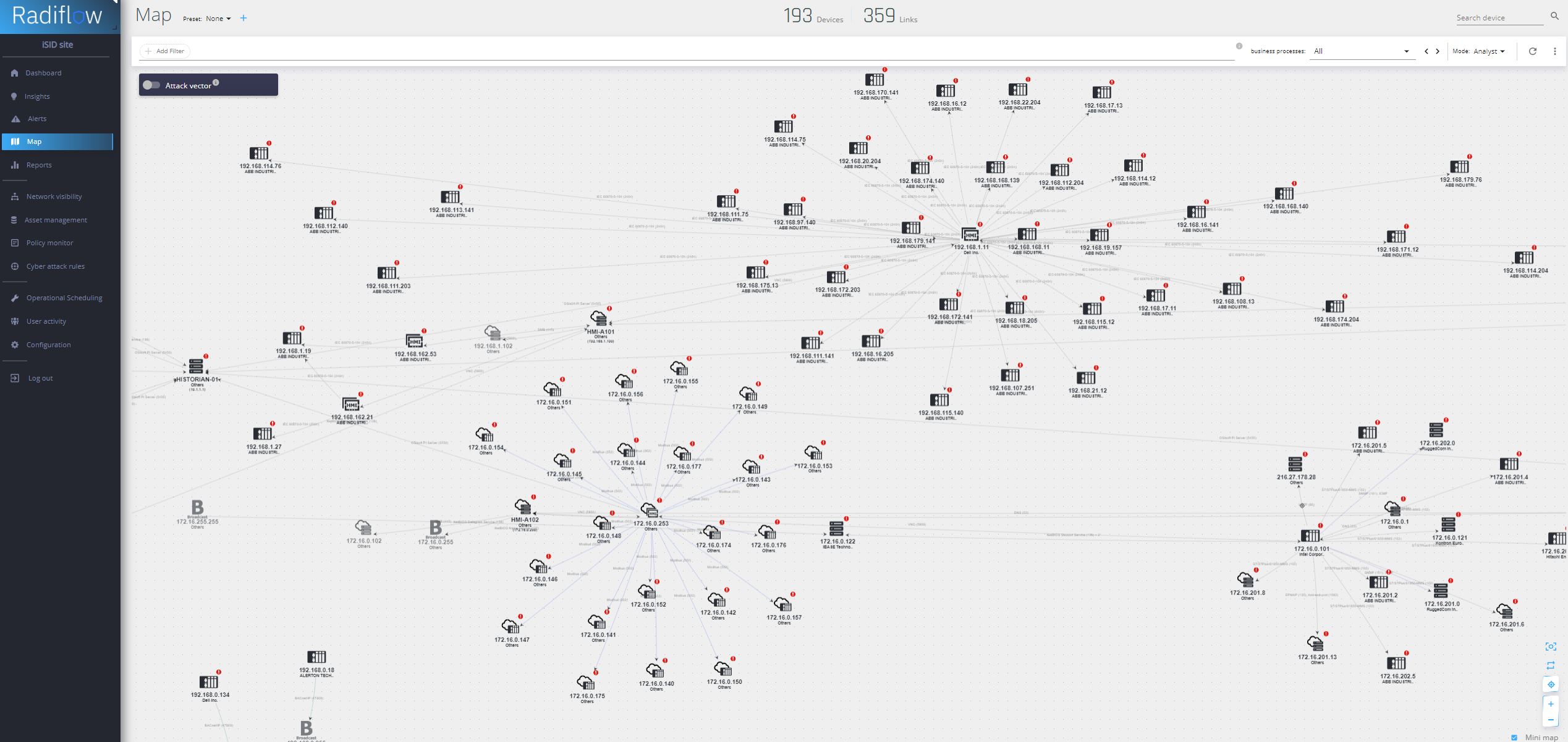
Malware Activity Detection: We use advanced algorithms and machine learning methods to identify and monitor suspicious activities in the network. Our solution continuously monitors traffic and analyzes behavior patterns to detect unusual and potentially harmful activities. Thanks to a combination of signature, heuristic, and behavioral analysis, we can quickly identify and respond to threats, including those that are new or previously unknown. Our goal is to provide organizations with maximum protection against malicious software and minimize the risk of security breaches.
-
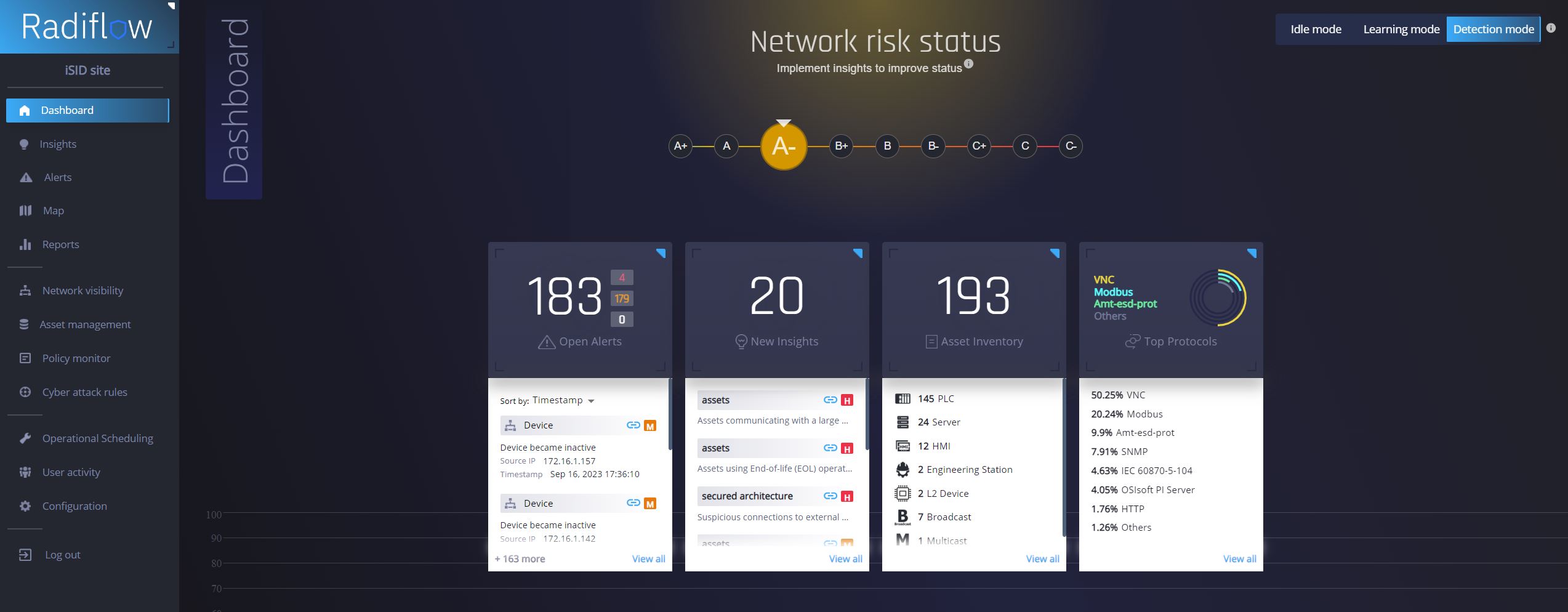
Personalized Solutions: In the field of anomaly detection in OT networks, solutions tailored to the unique needs of each organization are crucial. These solutions include a thorough analysis of customer needs, customization of detection algorithms, integration with existing systems, training, and regular updates. With them, organizations can effectively counter cyber threats and enhance the overall security of their OT networks.
-
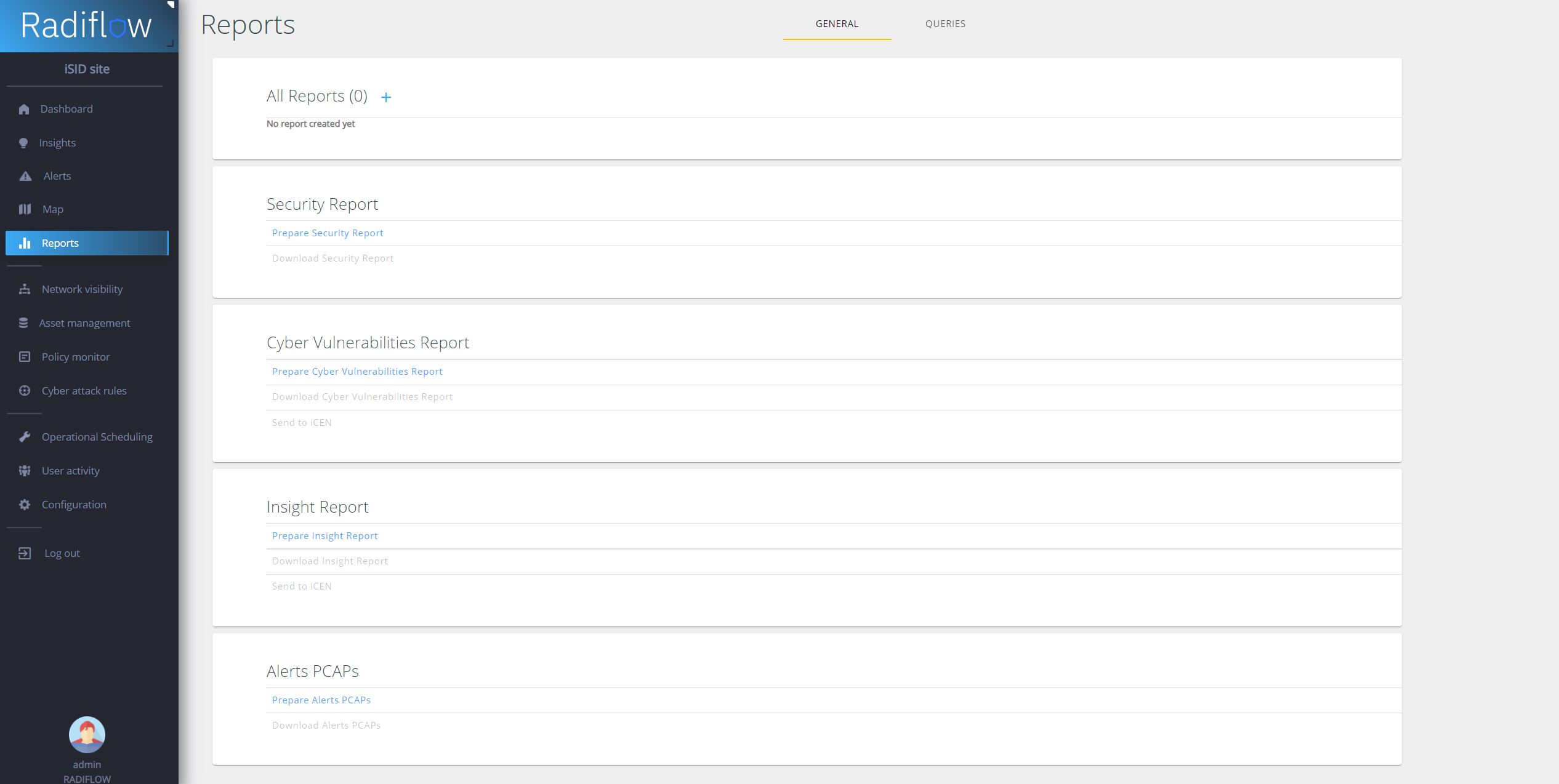
Expert Support: In today's rapidly changing digital age, maintaining an OT network resilient to various threats is very time-consuming. It's not just about protection against sophisticated cyberattacks, but also ensuring that the network is protected against human errors and complies with all legislative regulations. This requires not only a deep understanding of one's own infrastructure and comprehensive knowledge of changing bureaucracy but also continuous analysis of the latest models and techniques of cyberattacks. Mastering all these aspects can easily and very quickly deplete your human resources. Therefore, leave all these complex tasks to us. With our team of experts, you can be assured that your OT network will not only be protected but also optimized in accordance with the latest standards and practices in cybersecurity.
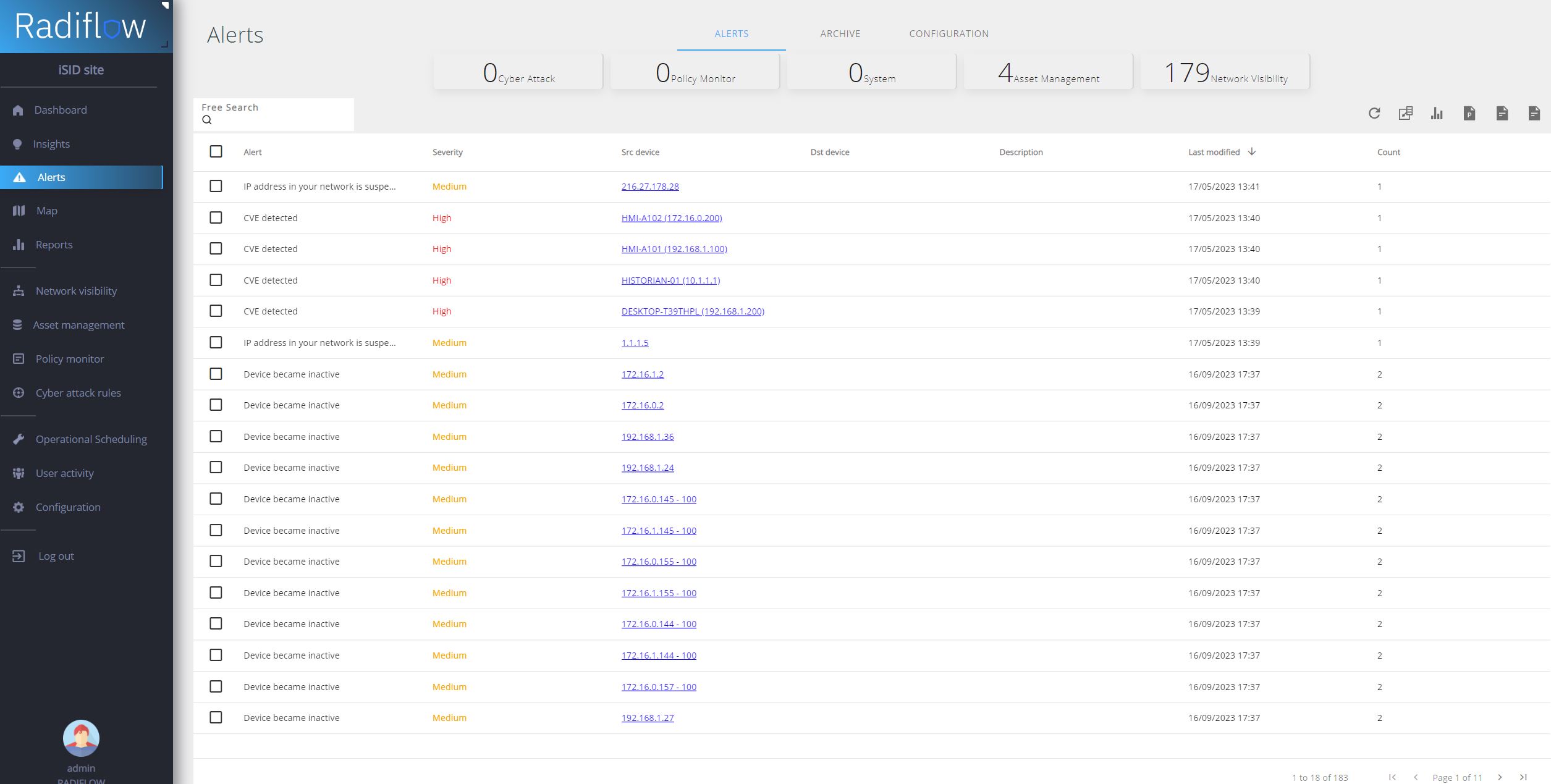
Conclusion
In today's digital age, the cybersecurity of OT networks is more important than ever before. With the increasing number of threats, it is essential to have a reliable solution for anomaly detection that can protect your critical assets. Together, we can ensure that your OT networks will be secure and protected against potential threats.
Related posts
 Risk Management and NIS2: The Key to a Secure Digital World
Risk Management and NIS2: The Key to a Secure Digital World
 Evaluation of the Current State of Your Infrastructure
Evaluation of the Current State of Your Infrastructure





