-
MenuBack
-
Products
-
-
-
-
-
-
Municipal services and retail
- All-in-One Touch Computers & Kiosks
- iCity Service & iRetail Solution
- POS & Tablets
- Signage & Edge Computers
-
Connections
-
Cellular Routers and Gateways
- 4G & 5G Entry Level Industrial Routers - ICR-2000
- 4G Powerful Routers - ICR-3200 & SmartFlex
- 5G & 4G Connectivity Gateways - ICR-1000
- 5G & LTE Advanced High Speed Routers - ICR-4000
- Accessories
- Antennas
- Dual Module 4G Routers
- EN 50155 Railway 4G Routers
- Entry Level 4G Routers
- Entry Level 4G Routers & IoT Gateways
- Flexible 4G Routers & IoT Gateways
- High Speed 4G/5G Routers & Edge Computing Gateways
- Industrial LAN Routers (Wi-Fi Optional)
- Modular 3G Routers
- Modular 4G Routers
- Power supplies
- Robust 4G Routers & IoT Gateways
- Software
- Wired LAN Routers
- Ethernet / Serial Device Servers
- Fiber & PoE Converters, Injectors, Extenders
-
Industrial Ethernet Switches
- EN50155 Ethernet Switches
- EN50155 Ethernet Switches: EKI-9500
- IEC61850-3 Ethernet Switches
- Industrial PoE Switches & Solutions
- M12 Ethernet Switches: EKI-9500
- Managed Ethernet Switches
- Managed Ethernet Switches (Entry-level)
- Managed Ethernet Switches (Entry-level): EKI-5000
- Managed Ethernet Switches: EKI-5700/7000/8000/9000
- Managed Ethernet Switches: EKI-7000/8000/9000
- N-Key automatic backup and restore
- Unmanaged Ethernet Switches
- Unmanaged Ethernet Switches: EKI-2000/5000
- Industrial Protocol Gateways
- Industrial Wireless and Gateways
-
Serial Communication
- Serial Communication Cards
-
Serial Converters/Isolators/Repeaters - ULI-200
- Data Tap/Splitter/Port Combiner - ULI-250/260
- RS-232 Isolated Repeater/Isolator - ULI-232 Series
- RS-232 to RS-422 Converters - ULI-223 Series
- RS-232 to RS-422/485 Converters - ULI-224 Series
- RS-232 to RS-485 Converters - ULI-226 Series
- RS-232/422 to TTL/Current Loop Converter - ULI-227
- RS-422/485 Isolated Repeaters - ULI-234 Series
- Serial Surge Suppressors - ULI-240 Series
- Serial to Fiber Converters - ULI-210 Series
- USB Converters/Isolators/Hubs - ULI-300/400
- Telematics Converters and Gateways
-
Cellular Routers and Gateways
-
-
-
Industrial automation
-
Industrial Automation
- Automation Controllers & I/O
- Certified Solutions
- Class I, Division 2 Solution
-
Data Acquisition (DAQ)
- 3U Communication Boards (MIC-3600 Series)
- 3U Data Acquisition and Control Boards (MIC-3700 Series)
- DAQ Cards
- DAQ-embedded Computer/Module
- DAQNavi
- GPIB
- iDoor Module(Mini PCIe)
- ISA DAQ Cards
- Modular DAQ System
- PC-104/PCI-104 DAQ & Communication Cards
- Signal Conditioning Modules and Terminal Boards
- USB Modules
-
Embedded Automation Computers
- Advantech iDoor Module
- Compact Embedded Box IPC
- Compact Embedded Box PC
- Din-Rail Automation Computer, UNO-1 Series
- Din-Rail Control IPC
- Expandable Automation Computer
- Expandable Automation Computer, UNO-3 Series
- Explosion-Proof Computer
- Industrial IoT Edge Gateway
- Rackmountable Automation Computers for Power Substations
- Standmount Embedded Box PC, UNO-2 Series
- UNO Accessories
- Gateways & Remote Terminal Units (RTUs)
- Human Machine Interfaces
- Machine Automation
- Panel PC
- Power & Energy
- Remote I/O
- SoftLogic Software
- Software Development Kits
- WebAccess Software & Edge SRP
- Wireless I/O & Sensors
-
Industrial Automation
-
Certified peripherals
-
Certified Peripherals
- Active CPU Cooler
- CPU
- Display
- DRAM Memory Module
- Expansion Card
- Flash Card
- Graphics Card
- Hard Drive
- Keyboard
- Mobile Rack
- Mouse
- Network Card
- Optical Drive
- Passive CPU Cooler
- Power Supply
- Rackmount Kit
- RAID Controller
- Software
- Solid State Drive
-
Certified Peripherals
-
Embedded computing
-
Embedded Computing
- AIoT Software, Distribution & Services
- Application Focus Embedded Solutions
- Arm-Based Computing Platforms
- Cable Accessories
- Computer On Modules
- Digital Signage Players
- Edge AI & Intelligence Solutions
- Embedded PCs
- Embedded Single Board Computers
- Embedded Software
-
Fanless Embedded Computers
- ARK Ultra Rugged Series
- ARK-1000 Series: Ultra Slim Fanless Embedded Computers
- ARK-2000 series : Easy I/O Flexibility Fanless Embedded Computers
- ARK-3000 Series: High Performance Fanless Embedded Computers
- ARK-6300 Series: Mini-ITX Series Fanless Embedded Computers
- ARK-7000 Series: Extreme Performance Edge Servers
- iDoor Module Mini PCIe Expansion Kit
- Storage Modules
- Gaming Platform Solutions
- Industrial Display Systems
- Industrial Flash & Memory Solutions
- Industrial Motherboards
- Industrial Wireless Solutions
- Wireless ePaper Display Solutions
-
Embedded Computing
-
-
-
-
-
-
-
Ethernet Extenders
-
Industrial routers
-
-
-
Wireless & Cellular
-
Modems
-
Accessories
-
-
-
-
-
-
-
Ethernet switches
-
-
-
Media convertors
-
Industrial connectivity
-
-
-
Wireless data transfer
-
-
-
-
-
-
-
Routers and Gateways
-
-
-
Icom Connectivity Suite
-
-
-
Icom Data Suite
-
-
-
-
-
- About us
- News
- Industrial areas
- Services
- References
- Support
- Contact
Risk Management and NIS2: The Key to a Secure Digital World
Risk Management and NIS2: The Key to a Secure Digital World
In a time when digital security is at the forefront of our concerns, adopting standards and measures becomes a necessity for businesses of all sizes. One of the most current and crucial measures in the EU is the Directive on the security of network and information systems, known as NIS2. For businesses to meet these regulatory requirements and adhere to them, thorough analysis and risk management are essential. Westercom Ltd. comes with expert services dealing specifically with NIS2 and risk management, helping organizations achieve not only compliance but also strong cyber defense.
What is the NIS2 Directive?
The NIS2 Directive is a European directive designed to strengthen the cybersecurity of critical services in EU member states. It represents an updated and enhanced framework that builds on the original NIS Directive from 2016. NIS2 emphasizes the need to strengthen national cyber capacities, increase cooperation between member states, and ensure that both public and private sectors are properly prepared to face cyber threats. More information can be found here.
Why is risk management so important?
For active and effective management of cyber threats, it is essential to conduct regular risk assessments. Risk management helps organizations identify potential weaknesses, threatened assets, and possible impacts of cyber incidents, which is essential for creating appropriate security measures.
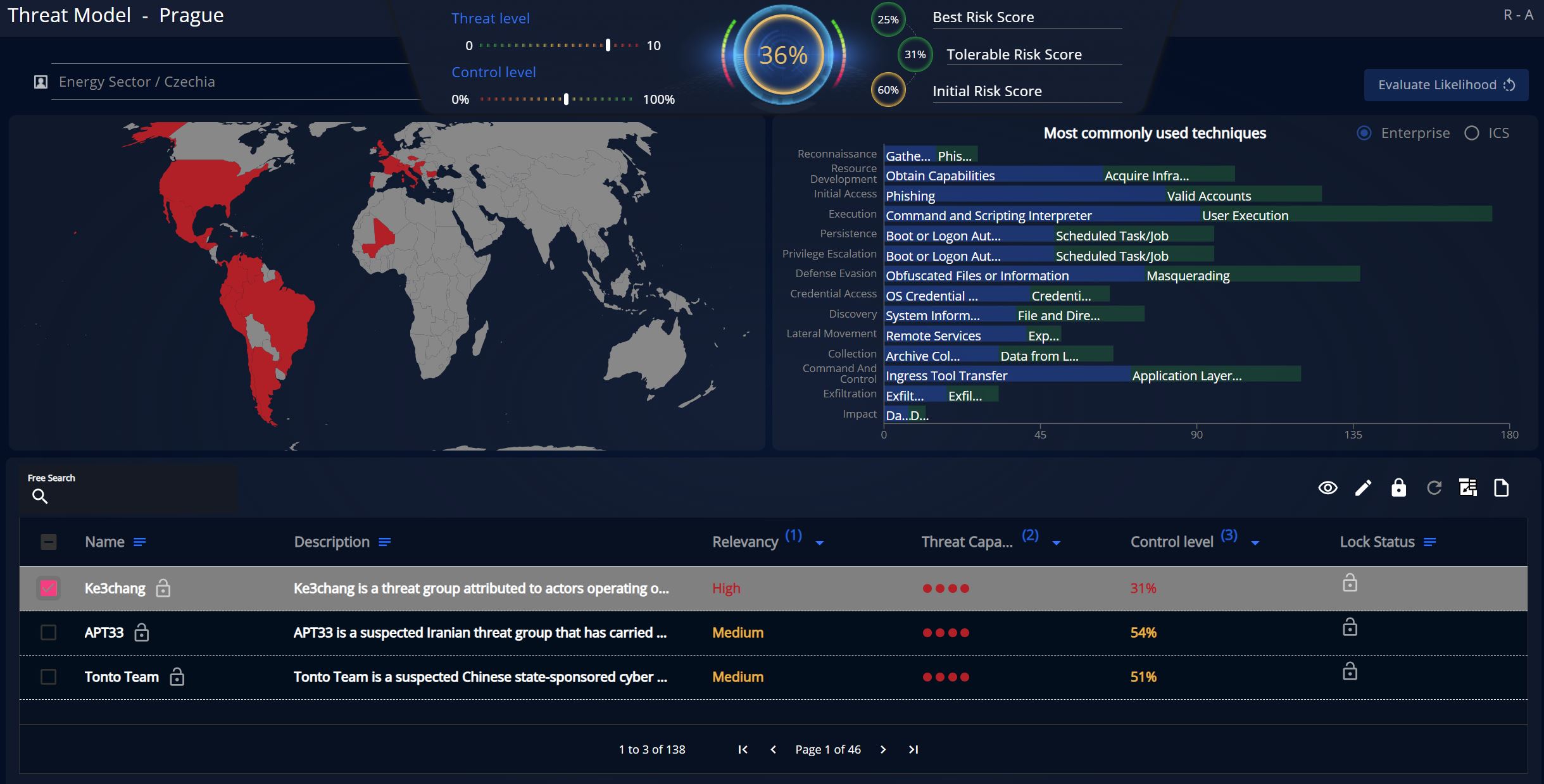
What obligations does NIS2 impose?
This directive emphasizes a proactive approach to cybersecurity, where not only the response to incidents is important, but primarily their prevention. The NIS2 Directive brings a number of new obligations for providers of essential and digital services. The main obligations include:
-
Risk Assessment: Enterprises must regularly conduct and update risk assessments to identify threats and vulnerabilities in their information systems.
-
Security Measures: Based on risk assessments, appropriate technical and organizational measures must be adopted to ensure the security of networks and information systems.
-
Incident Reporting: In the event of a security incident, enterprises are obliged to inform the relevant national authorities within 72 hours of its detection.
-
Cooperation: Enterprises are required to cooperate with national and international authorities in the field of cybersecurity and share information about threats and incidents with them.
-
Regular Reviews: The directive requires enterprises to regularly review and update their security policies and procedures in line with the latest standards and recommendations in the field of cybersecurity.
Who is the NIS2 Directive for?
The NIS2 Directive was created with the aim of strengthening cybersecurity within the European Union. Its main goal is to protect critical infrastructures and services that are essential for the daily functioning of society and the economy. Specifically, it applies to:
Providers of Essential Services (OES)
These organizations operate in areas that are key to society, such as:
- Energy (e.g., electricity, oil and gas industries)
- Transport (e.g., aviation, rail, road, and maritime transport)
- Banking
- Healthcare
- Drinking water
- Digital infrastructure
Digital Service Providers (DSP)
Companies that offer online platforms, search engines, and cloud services.
It is important to note that although the directive sets a general framework for the EU, specific implementations and requirements may vary slightly in individual member states. Therefore, it is essential for organizations to turn to local experts and regulatory authorities to obtain specific information regarding their obligations.
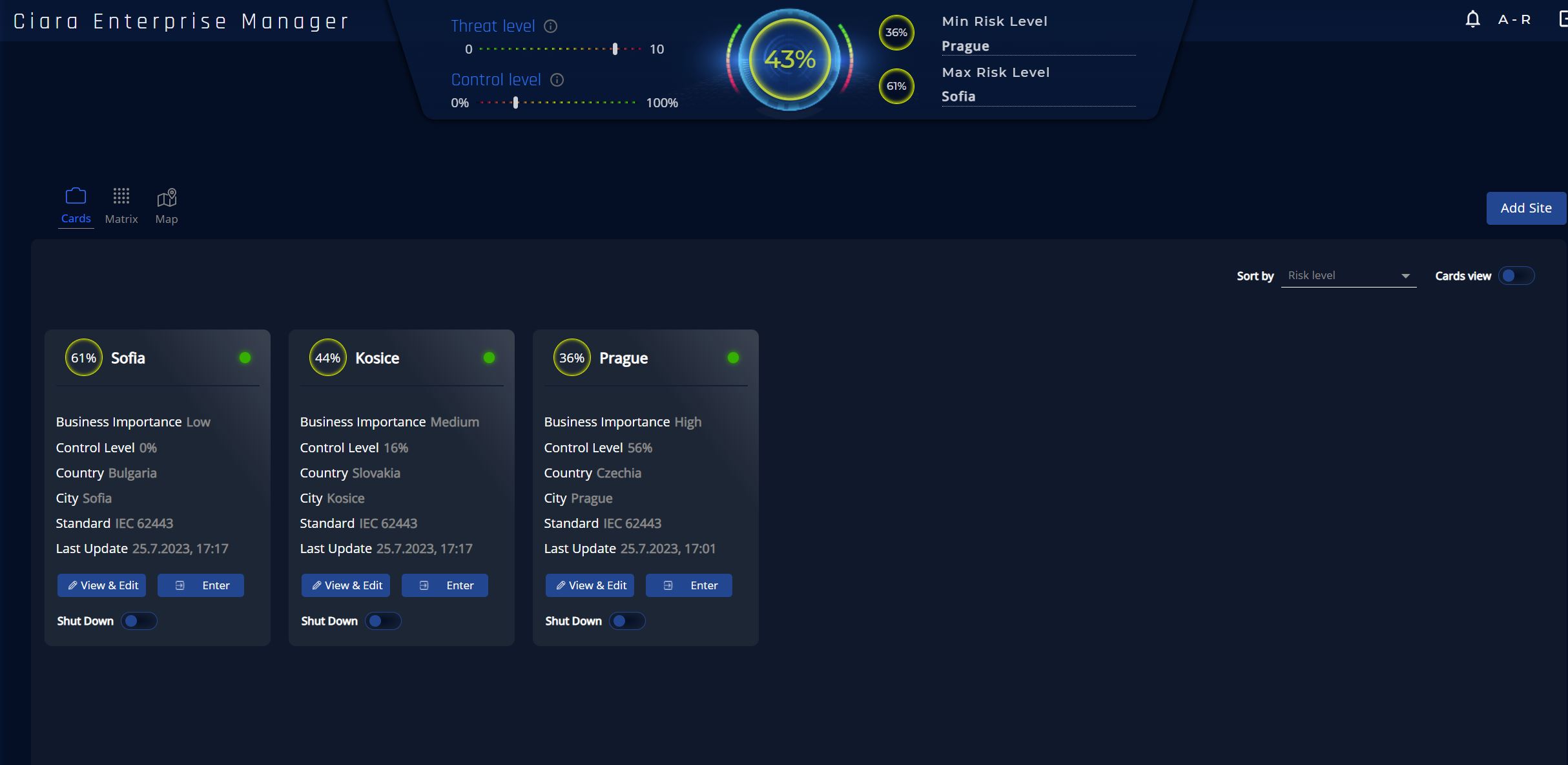
How can we help?
-
NIS2 Consultancy: We conduct in-depth consultations regarding the requirements of the NIS2 Directive. Our experts will help you understand the specifics of this directive and propose the best strategies for its implementation in your enterprise.
-
One-Time Assessment and Risk Management: Westercom will conduct a cybersecurity assessment according to the IEC 62443 standard to evaluate risks, threats, and measures to mitigate them. This assessment is a key step in ensuring the security of your systems and data. The process is carried out by our experts with extensive experience in the field of cybersecurity. The output of this service is a report that provides a detailed overview of identified vulnerabilities and recommended measures, in compliance with regulatory requirements.
-
Continuous Assessment and Risk Management: We will conduct an initial cybersecurity assessment according to the IEC 62443 standard and subsequently update the risk assessment document monthly. This regular updating will enable you to meet the requirements and obligations under the NIS2 Directive. Continuous risk management is the foundation for ensuring ongoing protection of your systems in a dynamically changing cyber environment.
-
Licensing: We will ensure a license for the CIARA Risk Assessment platform and also offer remote support. The license can be obtained either permanently or on a subscription basis. This platform and our support will enable you to effectively and continuously assess and manage risks in the field of cybersecurity.
-
Implementation: Installation of solutions in the cloud, virtual environment, or on physical hardware, optimization, and training. Thanks to our services, you can benefit from continuous risk assessment, which is automatically processed.
-
Professional Services: For further analysis of conducted risk assessments and the creation of a cybersecurity plan. This plan will serve to improve your position in the field of cybersecurity in the short, medium, and long term.
-
Ongoing Support: Once strategies and plans are established, our work does not end. We offer ongoing monitoring and updates to always keep you a step ahead of potential threats and stay in line with the evolution of the regulatory environment.
-
Industrial Hardware: We can provide you with reliable hardware, optimized for the performance of necessary operations, but also suitable for often adverse to critical environmental conditions where most OT systems are located.
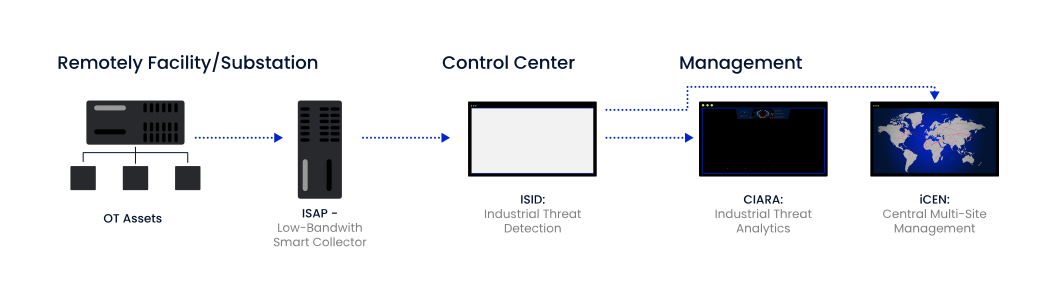
Conclusion
In today's rapidly changing digital world, it is essential for businesses to be equipped not only with appropriate tools and strategies but also with a deep understanding of the regulatory environment. We will become your reliable partner in the field of NIS2 and risk management. Together we can ensure that your organization is not only in compliance with the directive but is also stronger and better prepared to face future cyber challenges.
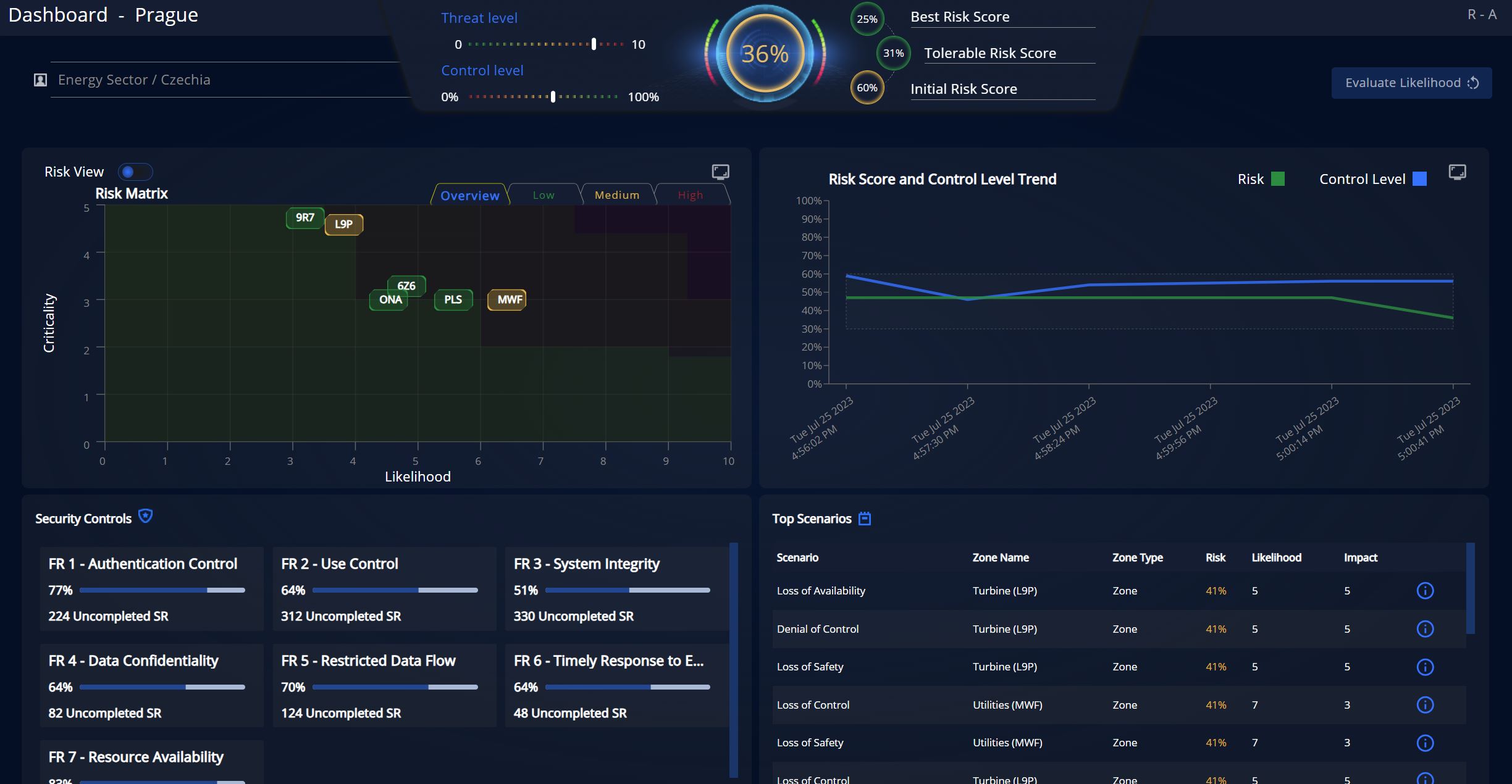
Related posts
 Anomaly detection in OT networks: a key defence
Anomaly detection in OT networks: a key defence
 Evaluation of the Current State of Your Infrastructure
Evaluation of the Current State of Your Infrastructure





